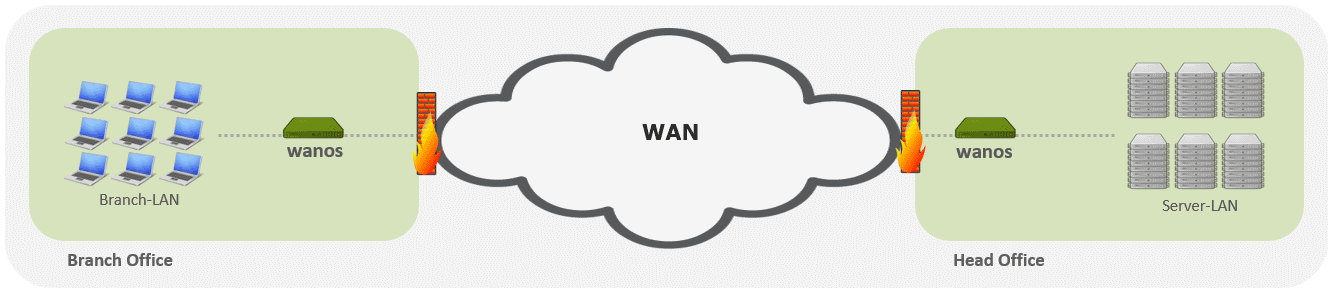
The WAN Optimizer is compatible with the Firewall on the LAN side or the WAN side of the bridge. When the Firewall encrypts or tunnel traffic e.g. IPsec or a GRE tunnel, then the Firewall must be on the WAN port side of the bridge.
Things to know about Firewalls
- When Firewalls are doing encryption like an IPsec VPN then the Wanos device needs to be on the user LAN side to optimize the traffic before it’s encrypted. In other words, when the Firewall is between the Wanos appliance and the user LAN, this is supported as long as the Firewall is not encrypting or encapsulating traffic.
- When the Firewall is on the WAN side and the filter rules are very strict, some configuration may be required to allow the Wanos optimized traffic through. This is normally TCP Option 76 and IPComp (IP Proto 108).
- When the Firewall is on the WAN side and NATting traffic, UDP Encapsulation on the Wanos devices may be required.
- Wanos uses the TCP option 76 only in SYN and SYN-ACK packets of each TCP connection. This is used for auto-discovery.
- In bridge mode with the firewall on the WAN side, the firewall should have TCP sequence number randomization disabled.
- Tunnel mode can be used when users are not in control of the Firewalls. It gives them a last resort option when they can’t implement the recommended/required firewall changes.
Wanos as a WAN accelerator is deployed in WAN environments where typically a Firewall might also be found e.g.:
The firewall may require a specific configuration to permit TCP option 76 for Wanos auto discovery to be operational. This is only needed if the firewall is in the path between Wanos devices and overwrites TCP Options. A firewall that is configured to overwrite TCP Options will replace options with a No-Option (nop) value and hence produce the following tcpdump output:
[mss 1320,nop,nop,sackOK,nop,wscale 11,nop,nop,nop,nop,nop,nop,nop,nop,nop,nop,nop,nop,nop,nop,nop,nop]
In this case the following sample configuration can be used on Cisco ASA/PIX:
access-list wanos_tcp extended permit tcp any any class-map tcp-traffic match access-list wanos_tcp tcp-map allow-probes tcp-options range 76 78 allow policy-map global_policy class tcp-traffic set connection advanced-options allow-probes service-policy global_policy global
Examples where peer discovery may fail
- Firewall or SAT modem that strips TCP Options. Example: Option 76, Window scaling, and Selective ACKs.
- The firewall that can’t NAT/PAT proto 108.
- Traffic traversing the WAN passes through a satellite or other device that strips off TCP options, including those used by auto-discovery.
- Traffic traversing the WAN goes through a device that proxies TCP connections and uses its TCP connection to transport the traffic. For example, some satellite-based WANs use built-in TCP proxies in their satellite up-links.
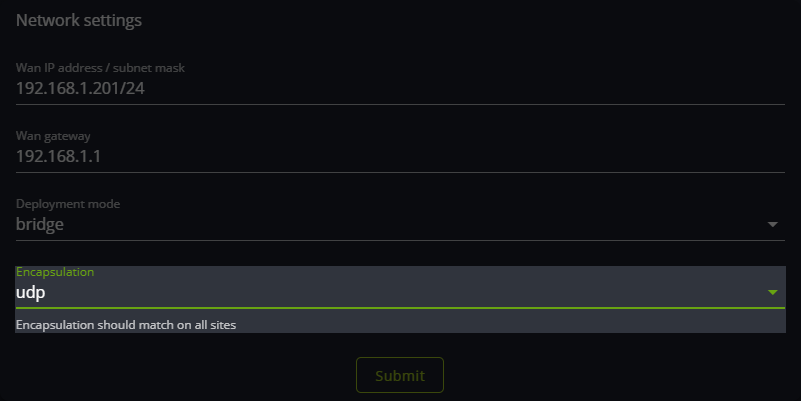
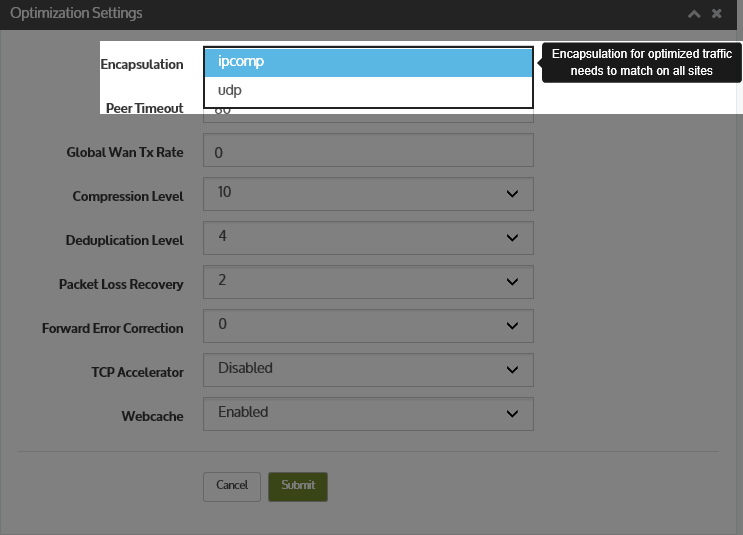
- Enable UDP Encapsulation by setting the UDP encapsulation in the Wanos.
Notes when enabling UDP encapsulation:
- All sites require this option configured.
- Introduces an additional overhead and processing.
Please post a sample config in Wanos Forums if you use a different firewall and have to configure a similar policy.