TCPdump is availble.
Review if wan0 and lan0 interfaces were configured correctly. A command-line tcpdump -i wan0 is available.
Example of SSH traffic on wan0
root@wanos:~# tcpdump -i wan0 tcpdump: WARNING: lan0: no IPv4 address assigned tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on lan0, link-type EN10MB (Ethernet), capture size 65535 bytes 05:12:15.593858 IP 192.168.5.2.ssh > 192.168.5.254.63976: Flags [P.], seq 1361930306:1361930418, ack 4233858220, win 1165, length 112 05:12:15.594880 IP 192.168.5.254.63976 > 192.168.5.2.ssh: Flags [.], ack 112, win 13235, length 0 05:12:15.595633 IP 192.168.5.2.ssh > 192.168.5.254.63976: Flags [P.], seq 112:320, ack 1, win 1165, length 208
We can check if we are sending probes in TCP Options header.
root@wanos:~# tcpdump -i wan0 -X | grep "0x7a69"
If we can see any packets:
root@wanos:~# tcpdump -i wan0 -X | grep mss | grep 0x7a69 tcpdump: WARNING: wan0: no IPv4 address assigned tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on wan0, link-type EN10MB (Ethernet), capture size 65535 bytes 23:30:37.152005 IP wanos.org.http > 192.168.100.13.52610: Flags [S.], seq 83722653, ack 3204888463, win 14600, options [mss 1320,nop,wscale 8,unknown-76 0x7a69], length 0
Use Wireshark to dump traffic and do thorough examination in the log file.
tcpdump -i wan0 -s 0 -w dump.pcap
For SYN TCP packet check the “Riverbed probe” options.
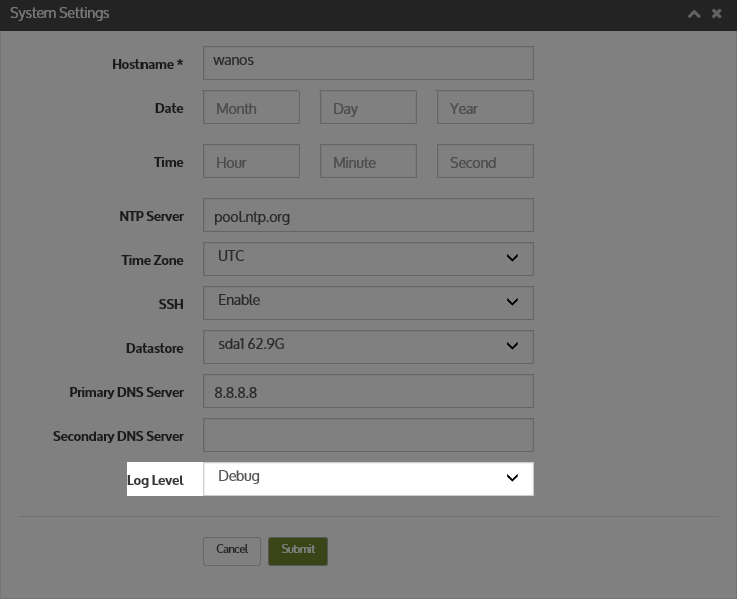
Now that we know that peer discovery probes are being sent we can verify the logs. Switch from Informational to Debug and check for Peer Alive messages.
Log Location
In WCM
Device > Diagnostics > Logging
Local Web User Interface
Diagnostics > Logging