Although it is recommended to dedicate separate physical NIC's for lan0 and wan0, in certain cases only a single NIC might be available for Wanos and worth the compromise.
Things to consider when only one physical NIC is available:
1) Performance compromise, traffic will traverse the same interface at least twice
2) The bridge appliance will bridge traffic from the lan0 to the wan0 and vice versa. Bridge loops can still occur.
3) To split the single NIC traffic into two virtual interfaces, two VLAN's are required, the inside lan0 VLAN and the outside wan0 VLAN.
4) Promiscuous mode needs to be enabled on portgroup level and not vswitch level. In other words promiscuous is disabled (reject) for the vswitch and enabled for the outside and inside VLAN's.
5) Vmware is not native VLAN aware. Use normal VLAN's to ensure the traffic flow is predictable.
Caveats:
1) On a Cisco switch and possibly other spanning-tree enabled switches, 'spanning-tree bpdufilter enable' is required on the trunk interface between the host NIC and the switch.
2) The switch can't also be the gateway for the inside lan0 VLAN if it's a Layer3 switch. On the switches tested, frames were implicitly dropped on the trunk if the destination MAC was also the one of the switch local MAC addresses. This is either a feature or a bug, either way take note that the gateway needs to be another L3 switch, router or firewall.
Example:
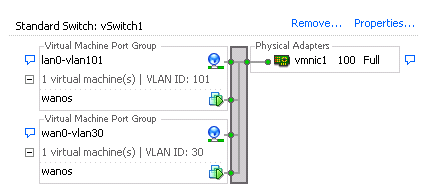
Switch config:
interface FastEthernet0/5
switchport trunk encapsulation dot1q
switchport trunk allowed vlan 30,101
switchport mode trunk
spanning-tree portfast trunk
spanning-tree bpdufilter enableCredit goes to spoonzw